When installing a certificate on Apache web server, you might receive an error “SSL Library Error: 185073780 error:0B080074:x509 certificate routines:X509_check_private_key:key values mismatch” during restart of Apache service.
Most often, this error appears if you are using an incorrect private key along with the certificate you received from the Certificate Authority. In order for Apache to accept certificate, it should be used with the private key generated along with the CSR code submitted for the certificate activation.
You can check whether the certificate matches the private key using the following openssl commands:
openssl x509 -in /path/to/certificate.crt -noout -modulus | openssl sha1
openssl rsa -in /path/to/private.key -noout -modulus | openssl sha1
The first command is applied to the certificate file, which you received from the Certificate Authority. The second one is for the private key.
Note: Make sure you indicate the correct path to the certificate and key files. You can take either relative or absolute path.Alternatively, you can check sha256 or md5 moduli of the key and certificate pair, replacing the hash function at the end of the command.
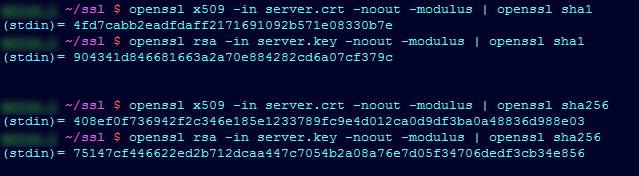
If the outputs of the commands differ (like in the screenshot above), this means that the chosen private key does not match the certificate.
You may also check whether the certificate matches the private key using this online tool. Copy the contents of the certificate and key files to the corresponding fields in the form and click “Match”. The site will show whether or not the certificate can be installed with the provided private key.
You will need to find another private key file on the server. The command below may help you:
find / -name “*.key”
This command will find all files on the server with .key extensions. Make sure you are logged in as root user, otherwise you may need to add sudo in front of the command.
Once the keys are found, check their moduli using the openssl rsa command listed above to locate one that matches.
If a private key with a modulus matching the certificate cannot be found, a new CSR code will need to be generated and the certificate reissued. Refer to these instructions on how to generate a new CSR code on your server and reissue the certificate.
One more possible cause of the error might refer to Apache starting from version 2.4.8.SSLCertificateChainFile directive became obsolete with version 2.4.8, when SSLCertificateFile was extended to also load intermediate CA certificates from the server certificate file. It allows the certificate file to contain the certificate as well as intermediate certificates. It is important that the end-entity certificate issued for a domain is placed as the first certificate in this file, while intermediate certificates should be placed lower starting from the one that signs the end-entity certificate. Otherwise, you may also receive the key values mismatch error.
Usefulness
Updated
6/18/2016
Viewed
969 times
Comments
We welcome your comments, questions, corrections and additional information relating to this article. Your comments may take some time to appear. Please be aware that off-topic comments will be deleted.
If you need specific help with your account, feel free to contact our Support Team. Thank you.

